Traditional perimeter-based security models are increasingly inadequate in today's hybrid cloud environments. Zero Trust architectures offer a compelling alternative by removing implicit trust and continuously validating every stage of digital interaction. In this comprehensive guide, we'll show you how we've helped enterprises implement Zero Trust, reducing security risks while improving access performance.
Understanding Zero Trust Architecture
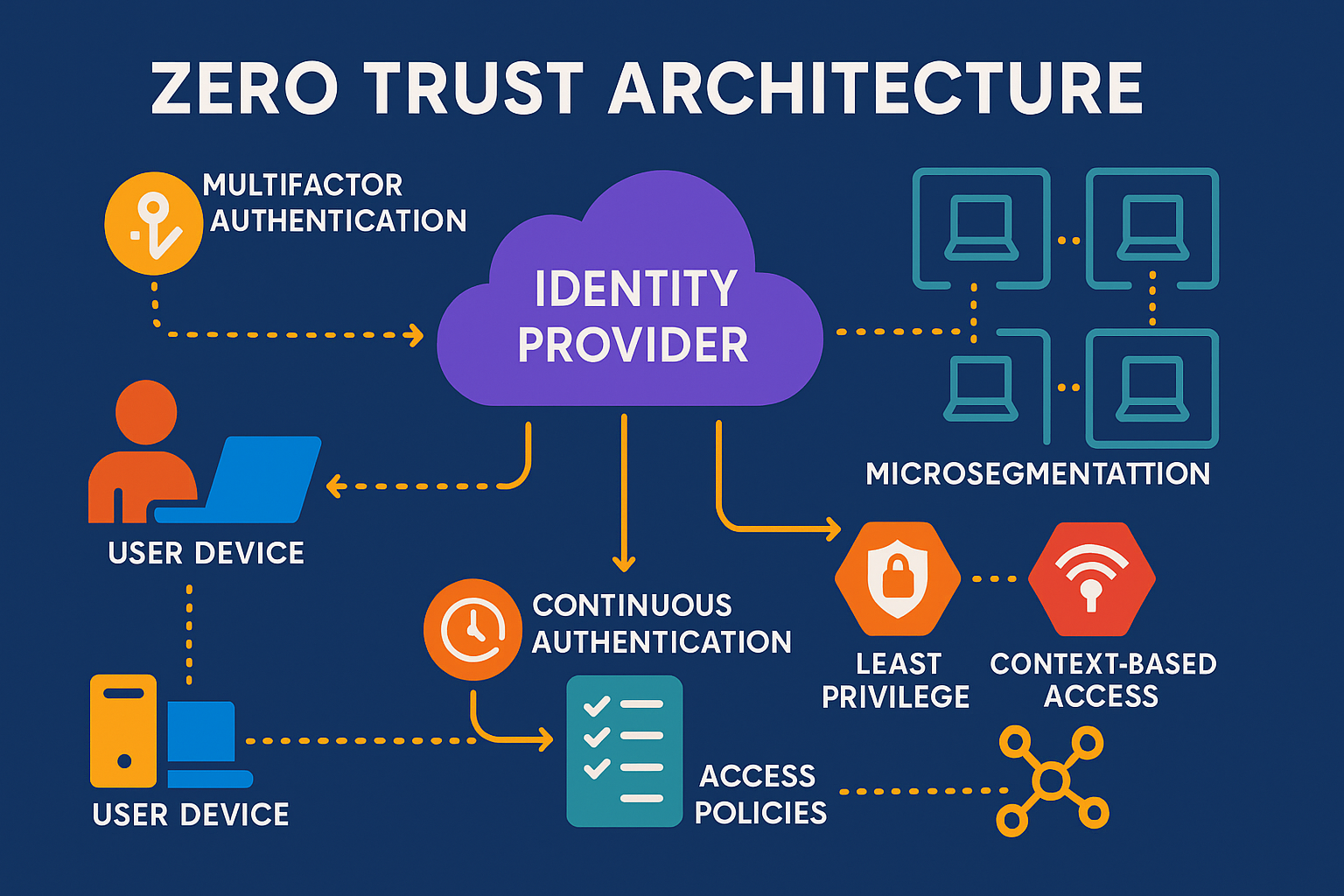
Zero Trust is a security concept centered on the belief that organizations should not automatically trust anything inside or outside their perimeters. Instead, they must verify anything and everything trying to connect to their systems before granting access.
The core principles of Zero Trust include:
- Verify explicitly: Always authenticate and authorize based on all available data points
- Use least privilege access: Limit user access with Just-In-Time and Just-Enough-Access (JIT/JEA)
- Assume breach: Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to improve security posture.
For enterprises with established security frameworks, Zero Trust isn't about replacing existing investments but evolving your approach to adapt to distributed workforces and hybrid cloud environments.
Building the Business Case
Before diving into implementation, it's crucial to articulate why Zero Trust makes business sense for your organization. We've found the following points particularly persuasive with executive stakeholders:
- Reduced attack surface: By implementing micro-segmentation and least privilege principles, organizations can reduce their vulnerable surface area by up to 70%.
- Improved user experience: Contrary to common misconceptions, well-implemented Zero Trust can enhance user experience by removing VPN bottlenecks and enabling seamless access to resources.
- Cost savings: In our client implementations, we've documented 30-40% reductions in security tool sprawl by consolidating systems and focusing on core Zero Trust capabilities.
- Regulatory compliance: Zero Trust directly addresses requirements in frameworks like GDPR, HIPAA, and PCI DSS around access controls and data protection.
"When we shifted from asking 'is this user on our network?' to 'do we have confidence this is the right user with the right authorization on the right device?' we fundamentally improved both our security posture and employee productivity." — CISO, Global Financial Services Client
Implementation Steps
Successfully implementing Zero Trust requires a strategic, phased approach. Through our work with dozens of enterprises, we've developed this six-step methodology:
1. Define Protected Resources
The first step is identifying your organization's critical data, assets, applications, and services. This inventory becomes the foundation of your protection strategy.
Key activities:
- Conduct data classification exercises to identify sensitive information
- Map business-critical applications and dependencies
- Document data flows between systems
- Prioritize resources based on business impact
Deliverable: Comprehensive resource inventory with sensitivity classifications
2. Map Transaction Flows
Understanding how users, devices, and systems interact with protected resources helps identify where to implement controls.
Key activities:
- Document how users access applications and data
- Map network traffic patterns between systems
- Identify authentication and authorization points
- Determine normal behavior patterns for baseline creation
Deliverable: Transaction flow diagrams with access patterns identified
3. Design Zero Trust Architecture
With resources and flows mapped, you can design a target architecture built on Zero Trust principles.
Key components to consider:
- Identity and access management (IAM): The foundation of user authentication and authorization
- Device management: Ensuring endpoint security and compliance
- Network controls: Micro-segmentation and software-defined perimeters
- Application security: API protection and runtime application security
- Data protection: Encryption, classification, and rights management
- Monitoring and analytics: Continuous monitoring for anomalous behavior
4. Create Policy Framework
Zero Trust requires detailed policies that define who can access what, under what conditions.
Policy considerations:
- User identity verification requirements
- Device health and compliance conditions
- Contextual access rules (time, location, risk signals)
- Data access and handling policies
- Continuous authorization requirements
Here's an example of a simple policy framework structure:
// Subject conditions
IF user.identity = verified AND
user.group IN allowed_groups AND
user.riskScore < threshold AND
// Device conditions
device.isManaged = true AND
device.complianceStatus = compliant AND
device.hasUpToDateAV = true AND
// Context conditions
request.location IN allowed_regions AND
request.time BETWEEN working_hours
// Then grant appropriate access
THEN grant_access(
resource,
minimum_required_permissions,
session_duration
)
ELSE
request_additional_authentication OR
deny_access
5. Select Solutions & Deploy
With architecture and policies defined, select and implement the appropriate technologies.
Key implementation areas:
- Identity solutions: SSO, MFA, privileged access management, and adaptive authentication
- Network solutions: Software-defined perimeter, micro-segmentation tools
- Device management: MDM/UEM solutions, posture assessment
- Data protection: Encryption, DLP, CASB solutions
- Monitoring: SIEM, XDR, behavioral analytics
Phased deployment strategy:
- Start with pilot groups and non-critical applications
- Incorporate user feedback to refine policies
- Gradually expand to more critical resources
- Run parallel systems during transition
- Decommission legacy systems once zero trust controls are validated
6. Monitor & Maintain
Zero Trust is not a "set and forget" implementation but requires continuous improvement.
Ongoing activities:
- Continuously monitor for anomalous behaviors and policy violations
- Update access policies as business needs change
- Conduct regular security assessments of the architecture
- Refine policies based on security incidents and near-misses
- Train users on secure practices within a Zero Trust environment
Case Study: Financial Services Implementation
For a global financial services client with 15,000+ employees, we implemented a Zero Trust architecture that replaced their traditional VPN infrastructure. The results included:
- 94% reduction in authentication-related helpdesk tickets
- 78% improvement in access request processing time
- 65% reduction in security incidents related to unauthorized access
- $3.2M annual savings from consolidated security tools
The implementation focused on identity-first security with contextual access controls. We began with non-sensitive applications and gradually extended to core banking systems.
Common Challenges
When helping clients implement Zero Trust, we consistently encounter these challenges:
- Legacy application integration: Applications that assume network-based trust can be difficult to adapt
- User resistance: Changes to access workflows may face pushback without proper communication
- Decision scope: Organizations often try to implement too many changes simultaneously
- Skills gaps: Zero Trust requires expertise across identity, networking, and application security
To address these challenges, we recommend:
- Using gateway solutions to wrap legacy applications with modern authentication
- Engaging users early with clear communication about security and productivity benefits
- Starting with high-impact, low-complexity use cases
- Developing skills through focused training and partnerships
Conclusion
Zero Trust represents a paradigm shift in how organizations approach security. By removing implicit trust and continuously validating access requests, companies can significantly reduce their risk exposure while improving user experiences.
The journey to Zero Trust is incremental and should be tailored to your organization's specific needs and risk profile. By following the six-step implementation approach outlined above, you can navigate this transformation while minimizing disruption and maximizing security benefits.
Remember: Zero Trust is as much about changing mindsets as it is about implementing technology. Success depends on executive support, clear communication, and a commitment to continuous improvement.
Need Help Implementing Zero Trust?
Our team of security experts can help you design and implement a Zero Trust architecture tailored to your organization's specific needs.
Schedule a Consultation