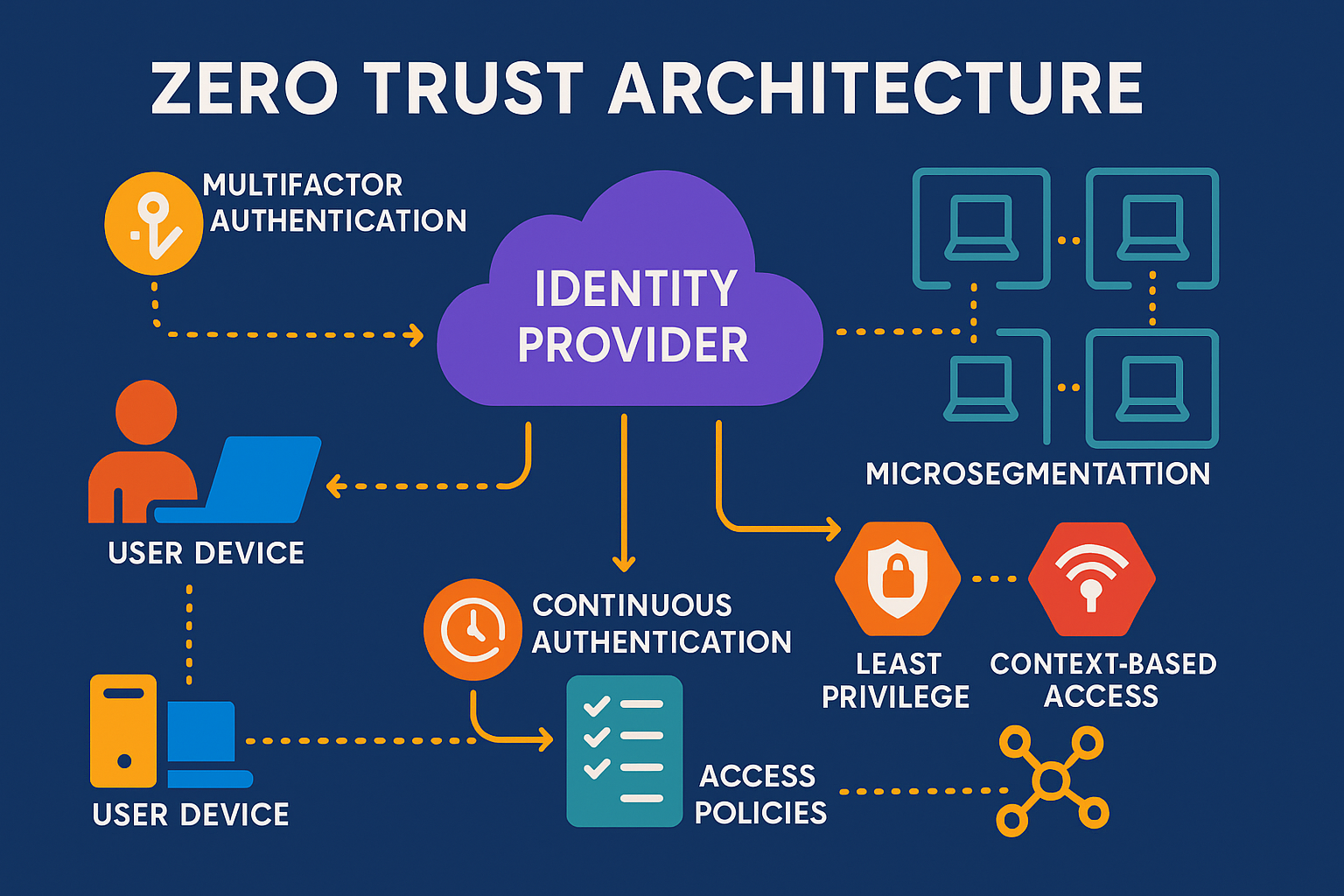
Zero Trust Architecture: Implementation Guide for Modern Enterprises
Traditional perimeter-based security models are increasingly inadequate in today's hybrid cloud environments. Zero Trust architectures offer a compelling alternative by removing implicit trust and continuously validating every stage of digital interaction. In this comprehensive guide, we'll show you how we've helped enterprises implement Zero Trust, reducing security risks while improving access performance.